
Dive into the Future with Vox Fibre Home Internet
Featured Fibre for Home Packages
Featured Fibre for Business Packages
Why Our Customers Love Us
Stuart Mckenna
Absolutely fantastic! Very friendly and accommodating. This is why I stay with Vox!!
Amanda Mthethwa
I’m very impressed with the fast and efficient service I received from Vox. Justin Bartes made the process of setting up my account and delivery of my router so easy! He was very helpful and answered every question I had. Thank you Justin and keep up the good work!
Mikaeel Mohamed
Vox. Great service. Simple choice. Signing up has never been easier. It's also the best and most convenient internet service provider we've found lately.
Liam Barreiro
Recently moved and been with Vox since moving. No issues. Fantastic customer service. Big thank you to Earl Slabbert for making things so seamless and stress free. Highly recommend!
Tanya Elario
Jonathan at Vox really came to the party on my recent move from a previous service provider. He handled a very frustrated customer (me) in absolutely the best way possible! He gave me a delivery date for my wifi to be connected and I am so glad to say that Jonathan and Vox delivered!! 10/10 for communication and service
Michael Kruz
Smooth and fast with getting connected. Great after service and friendly sales agents. great experience with Vox.
Daniel Mac Queen
Signed up with Vox, it's been a dream, from sales right through to installation. Service is great and haven't had nearly as many outages as with previous fibre provider.
Jodie Thomson
I recently had the pleasure of working with Christelle Vorster, an Account Executive at the contact centre at Vox Telecom, and I cannot express enough how impressed I am with her exceptional service. Christelle went above and beyond to assist me in moving and setting up an email box, and her dedication, patience, knowledge, and friendliness truly stood out.
Morné van der Watt
Really impressed with Vox, assistance was super quick. Ticket logged with Vuma and fixed within 2Hours rather than 3 days. Thank you Claude, if customer service was handled like this in SA we would be a better country.
Popular Products






Home Mesh Wi-Fi M4
Experience unmatched powerful Wi-Fi coverage with TP-Link Mesh technology
Starting from
R60 PM
*T&C's apply


Microsoft 365
Stay productive with these Microsoft Solutions
Starting from
R105 PM
*T&C's apply


Vobi Calling App
Stay connected with unlimited calls, video chats, and text messages
Starting from
R29 PM
*T&C's apply






Home Mesh X50
AI-Driven Mesh technology provides uninterrupted smart Wi-Fi
Starting from
R160 PM
*T&C's apply






Vox Power Solutions
Stay connected during Load-shedding and never let productivity come to a halt
Starting from
R85.33 PM
*T&C's apply






Home Mesh X20
Amplify Wi-Fi signals and expand coverage for a seamless connection
Starting from
R170 PM
*T&C's apply
Discover our connectivity products
Get the best connectivity and voice solutions with Vox to suit your everyday home or business needs
NEXT LEVEL HOME INTERNET
Fibre to the Home
Super-fast, reliable and affordable Internet is now a reality!
- Unlimited data, no more data top-ups
- Super-fast speeds that range from 4Mbps to 1Gbps
- Free to use router, Installation & Activation
- Save up to R4500 with Vox








FIRST CLASS BUSINESS CONNECTIVITY
Fibre to the Business
Build your business on the most reliable, scalable, versatile, and cost-effective connectivity solutions
- Light, premium and dedicated fibre options
- Tailored network designs
- Flexible contract terms
- 24/7 support, monitoring & maintenance
Save up to R5500 with FREE Installation with Frogfoot
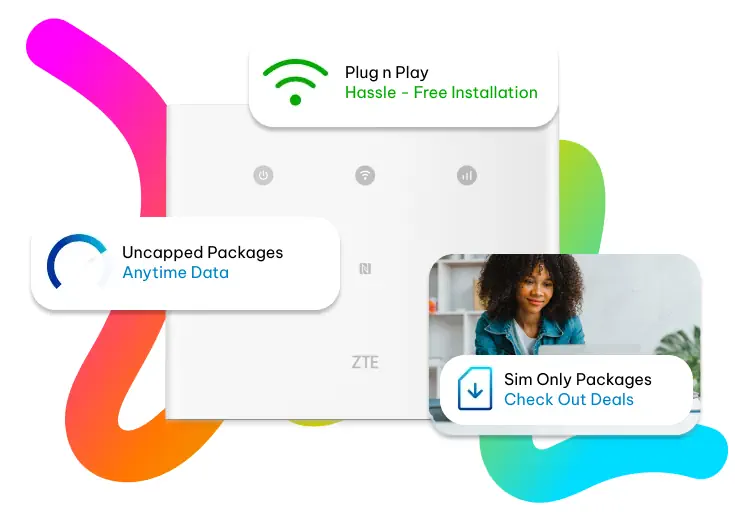
PLUG & PLAY WI-FI
Fixed LTE
Get connected to Fibre-like speeds without waiting for a fixed-line to be installed
- Plug & Play, Hassle-Free Installation
- Your Data, Your Way
- Month to Month Packages
- Choose between SIM Only and SIM + Router Rental options







UNLIMITED CALLING
Voice Solutions
Put an end to unnecessary high call rates and monthly bills with scalable Voice Solutions for your Home or Business
- Flexible VOIP solutions
- Unrivalled call quality – supporting a truly hybrid work environment
- Attractive pricing and saving options
- 24/7 support, monitoring & maintenance
Vox News
Read updates on our products, news from our product specialists or simply stay informed with our thought leader articles.
- Vox 4 Thought
- 13 May 2024
On the Couch or in a Different Country: Unlocking the Future of Work
Companies can at last dip their toes into a truly global talent pool without necessarily having to ask a potential new employee to change cities...
- Education
- 8 May 2024
The Need For (Internet) Speed
“I feel the need… the need for speed.” – Maverick and Goose, ‘Top Gun’, 1986 This iconic line from a now-classic movie – the...
- Uncategorised
- 29 April 2024
Starlink…what’s the deal?
Today, we talk Starlink. It’s the buzzword of the Nation now that Eskom is behaving. To the average person, it sounds like something Darth Vader…
- Vox 4 Thought
- 25 April 2024
Buck Up and Call More for Less With Vobi
As South Africans battle with current economic challenges, including price hikes on almost everything and continuing high unemployment numbers, the need for innovative strategies for consumers...
- Vox 4 Thought
- 19 April 2024
Flexible Work Spaces: What’s the Right Connectivity for Your Hybrid Environment?
It seems as though hybrid working arrangements are here to stay. This trend arguably offers the best of both worlds but – with employees being…
Top articles
- Vox 4 Thought
- 13 May 2024
On the Couch or in a Different Country: Unlocking the Future of Work
Companies can at last dip their toes into a truly global talent pool without necessarily having to ask a potential new employee to change cities...
- Education
- 8 May 2024
The Need For (Internet) Speed
“I feel the need… the need for speed.” – Maverick and Goose, ‘Top Gun’, 1986 This iconic line from a now-classic movie – the...
- Uncategorised
- 29 April 2024
Starlink…what’s the deal?
Today, we talk Starlink. It’s the buzzword of the Nation now that Eskom is behaving. To the average person, it sounds like something Darth Vader…
- Vox 4 Thought
- 25 April 2024
Buck Up and Call More for Less With Vobi
As South Africans battle with current economic challenges, including price hikes on almost everything and continuing high unemployment numbers, the need for innovative strategies for consumers...
We all strive to create the best products and services
Vox works in partnership with:










































































Let's get talking
Sign up to our newsletter
Get the latest Vox news and be the first to hear about our special offers















